BUSINESS
Strengthening Cybersecurity Posture with Advanced Vulnerability Management Workflows
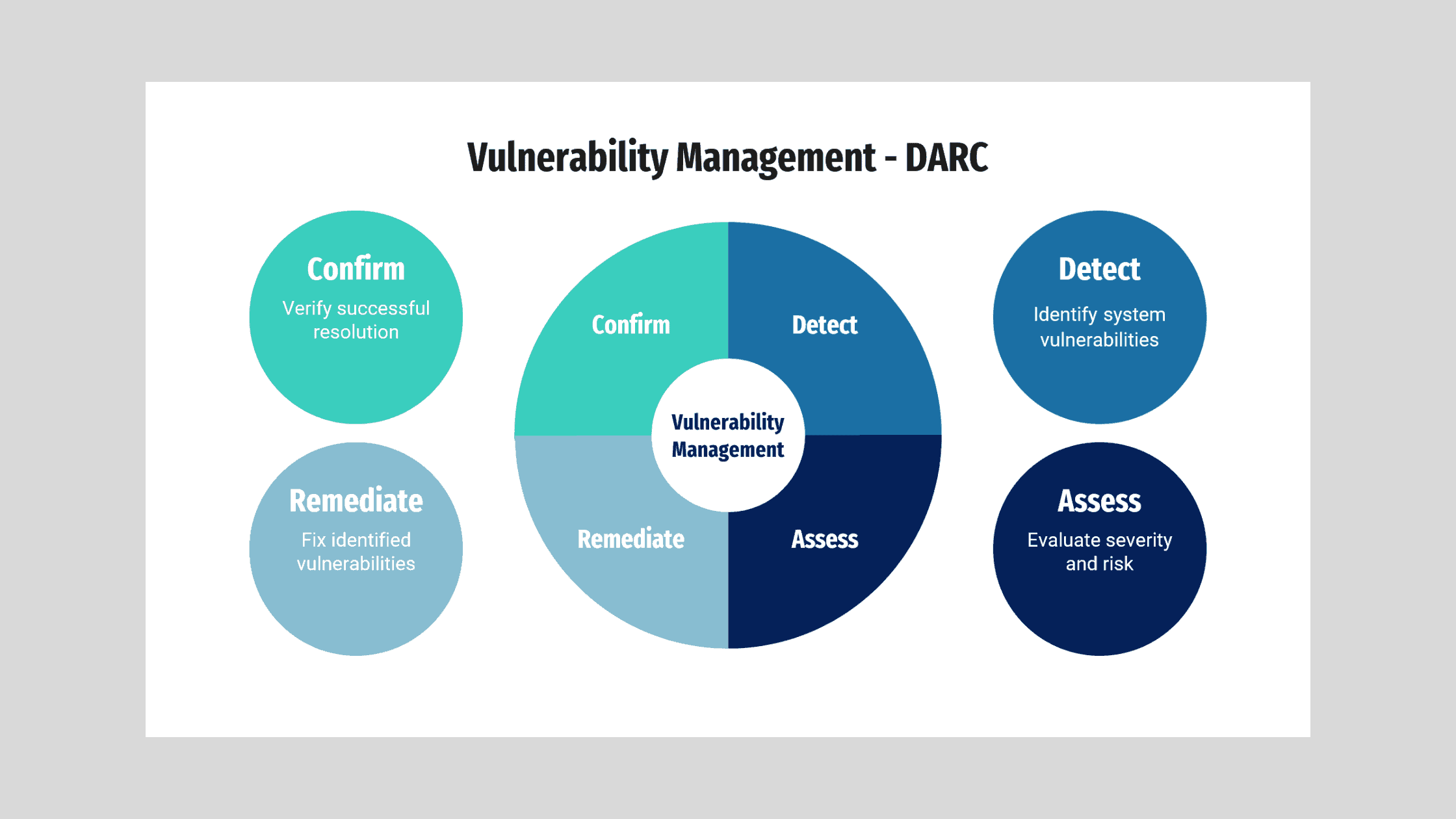
Table of Contents:
- Key Takeaways
- Understanding Vulnerability Management Workflows
- Identifying Vulnerabilities in Your Organization
- Prioritizing Vulnerabilities for Remediation
- The Remediation Process: Strategies and Best Practices
- Verification and Validation Post-Remediation
- Integrating Vulnerability Management into the Broader Security Strategy
- Future-Proofing: Adapting to Evolving Cyber Threats
- Best Tools and Resources for Vulnerability Management Workflow
- Legal and Regulatory Considerations in Vulnerability Management
- Conclusion: The Continuous Evolution of Vulnerability Management Workflows
Key Takeaways:
- Understanding the integral role of vulnerability management workflows in cybersecurity.
- Techniques for effective identification, prioritization, and remediation of vulnerabilities.
- Strategies for integrating vulnerability management within a comprehensive security program.
- Staying updated with evolving cyber threats is important to maintaining robust security protocols.
Understanding Vulnerability Management Workflows
An integrated security workflow encompasses a systematic approach to identifying, classifying, prioritizing, and addressing vulnerabilities within an organization’s technology environment. Implementing such methods is crucial to thwarting potential breaches and safeguarding digital information. A thorough vulnerability management plan lays out explicit steps to neutralize threats before they translate into actual harm. Workflows can vary from simple checklists to complex, automated processes involving a variety of cybersecurity tools.
Vulnerabilities come in many forms, ranging from software bugs to misconfigurations, all of which pose varying degrees of risk to the safety of organizational data. Thus, integrating a robust and repeatable process ensures both minor and critical vulnerabilities are addressed promptly.
Identifying Vulnerabilities in Your Organization
Crucial to the cybersecurity lifecycle is the ability to spot weaknesses before they can be exploited. To accurately identify these digital chinks in the armor, organizations deploy a multitude of tools—from static application security testing (SAST) to dynamic analysis (DAST) and beyond. By harnessing these technologies, it’s possible to obtain a holistic view of the organization’s security style, pinpointing exposure areas within applications, networks, and systems.
Beyond automated tools, manual tactics, including rigorous code reviews and penetration tests, provide additional layers of scrutiny. These assessments simulate hackers’ strategies, revealing potential entry points and markers for urgent revision. Regularly scheduled tests are fundamental, as they help unearth new threats that evolve as part of the changing cyber landscape, ensuring an organization’s protective measures are always current and effective.
Prioritizing Vulnerabilities for Remediation
After establishing a clear picture of existing vulnerabilities, the next critical step is determining which issues to tackle first. Not all security gaps exert the same level of threat to an organization’s infrastructure. Some vulnerabilities may grant attackers direct access to sensitive systems, while others might only have a peripheral impact. Factors that influence the prioritization of remediation efforts include the potential for data loss, system downtime, or the exploitation of critical infrastructure.
Effectively prioritizing vulnerabilities entails a comprehensive risk assessment, considering the likelihood of a security gap being exploited and the potential damage that could result. It’s a delicate balancing act that weighs the flaw’s severity against the resources available to address it—ensuring that the most critical weaknesses receive immediate attention. In contrast, others are scheduled for future remediation.
The Remediation Process: Strategies and Best Practices
Once vulnerabilities have been categorized and prioritized, the next phase is remediation. This process entails developing and deploying fixes to the identified issues through software patches, system updates, or alterations in network configurations. One of the best practices in remediation is maintaining a patch management policy, ensuring all software is up-to-date and resistant to known threats.
However, this journey from detection to remediation is often fraught with challenges. It’s critical to balance the speed of response with the necessity for accuracy in deploying fixes. Quick fixes may inadvertently introduce new vulnerabilities if not thoroughly tested. Sharing experiences of successful vulnerability resolution can provide useful insights for organizations looking to refine their remediation strategies.
Verification and Validation Post-Remediation
Remediating a vulnerability is not the endpoint of the management workflow; it’s critical to have mechanisms to verify and validate that the measures taken have effectively addressed the security gap. This often involves re-scanning the environment, conducting post-remediation penetration tests, or evaluating system logs for unusual activity that might indicate a lingering issue.
Continuous verification integrates assessment processes within routine operations, creating an environment where security becomes an ongoing concern rather than an afterthought. This ensures that fixes are deployed and remain effective over time, adjusting as needed to the changing threat landscape and organizational practices.
Integrating Vulnerability Management into the Broader Security Strategy
Vulnerability management can only stand with an organization’s aims for a truly resilient cybersecurity defense. It must be part of an integrated security strategy encompassing other components, such as endpoint protection, firewall deployment, and employee security awareness training. When each element works in concert, the organization’s security posture becomes more than the sum of its parts—forming a robust and responsive shield against cyber threats.
Furthermore, fostering a sense of shared responsibility for cybersecurity amongst staff members can go a long way. Through regular training and fostering a culture that values security, organizations can ensure that every layer of their defense—from the technology to the personnel—is optimized to detect and deter potential attacks.
Future-Proofing: Adapting to Evolving Cyber Threats
As attackers become more sophisticated, so must the defenses arrayed against them. Organizations must constantly refine their vulnerability management workflows for the latest security threats. Leveraging emerging technologies, like machine learning and artificial intelligence, can provide predictive capabilities to anticipate threats before they materialize.
Moreover, staying abreast of trends and emerging threats is not simply about purchasing the latest technologies; it also involves tapping into the collective wisdom of the cybersecurity community through forums, threat intelligence sharing, and industry-wide research compendiums. Organizations can ensure they are prepared to meet the challenges of tomorrow’s threat landscape head-on by continuously evolving and adapting security workflows.
Best Tools and Resources for Vulnerability Management Workflow
Investing in the right set of tools is critical for executing an effective vulnerability management workflow. Selections should be made based on compatibility, scalability, and the ability to integrate with other security platforms. Security solutions that offer comprehensive visibility, along with automated alerting and reporting capabilities, are often at the forefront of the industry.
Communities play a key role in staying informed and responsive. Online forums provide platforms for information sharing and discussion. At the same time, security research projects contribute valuable insights into new vulnerabilities and defensive techniques. Understanding the tools and resources at one’s disposal is pivotal to formulating a resilient security strategy.
Legal and Regulatory Considerations in Vulnerability Management
The cyber domain is not only about technical prowess; a complex web of legal and regulatory frameworks also governs it. These rules shape how organizations manage data security, privacy, and breaches. Complying with regulations such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA) is imperative for businesses operating internationally or handling sensitive personal data.
Navigating these waters requires diligence and often the assistance of legal experts who specialize in cybersecurity law. Ignoring these aspects can lead to severe penalties and damage an organization’s reputation.
Conclusion: The Continuous Evolution of Vulnerability Management Workflows
In conclusion, the realm of cybersecurity is a battlefield in continuous flux. Advanced vulnerability management workflows provide the strategies necessary to manage and anticipate the maneuvers of would-be attackers. As organizations embrace these comprehensive approaches, integrating cutting-edge tools and heeding regulatory requirements, they construct more reliable and robust systems capable of withstanding the onslaught of evolving threats. By accepting that the process of vulnerability management is never complete but a perpetual cycle of improvement, entities can forge ahead with confidence, knowing they are well-prepared to meet and mitigate future cyber challenges.
BUSINESS
Maintaining Peak Performance in Your Refrigerator: The Role of Ice Makers

Key Takeaways:
- Delving into the intricate workings of fridge ice makers.
- Providing comprehensive maintenance tips for consistent ice production and quality.
- Detecting potential issues that could lead to ice maker repair or replacement.
- Choosing an eco-friendly ice maker aligned with modern environmental standards.
- Benefiting from available informative resources on refrigerator maintenance and repair.
Introduction to Fridge Ice Makers
The refrigerator is essential in any contemporary kitchen, providing convenience and efficiency to culinary enthusiasts. The integrated ice maker is an exceptional feature that stands out for its ability to dispense chilled beverages instantly. This splendid facility eliminates the need for manual labor and the hassle of filling and emptying ice trays, making it an attractive addition to any home. To fully take advantage of the benefits of this marvelous feature and prolong its lifespan, users must gain a comprehensive understanding of its mechanics and maintain it with diligence. Users can have a constant supply of ice with this remarkable appliance.
How Do Ice Makers Work?
The process of how a refrigerator’s built-in ice maker, like the one found on PartSelect.com, works is genuinely fascinating. Even though it may seem like it operates quietly in the background, the process it goes through to produce ice is dynamic and precise. First, an electrically-controlled valve opens, allowing household water to flow into the ice mold. Then, a built-in thermostat determines when the ice is suitably frozen. At this point, heating coils briefly warm the molds to loosen the ice, ensuring that the cubes can be easily dispensed. Finally, a motor thrusts the ice cubes into a collection bin, where they are ready to be used at any time. This process is automatic and repeats cyclically, ensuring a continuous supply of ice for your convenience. It is important to note that the quality of the components used in the process is crucial in determining the reliability of the ice maker.
Regular Maintenance for Ice Makers
Regular maintenance is crucial to ensure an ice maker’s optimal performance and extended lifespan. Taking simple, proactive measures that can have a profound impact is essential. Homeowners should clean the ice bin with warm water and mild detergent periodically to remove old ice residues and eliminate germs that may affect ice quality or cause health risks. If the ice maker has a water filter, it’s advisable to replace it at the intervals recommended by the refrigerator manufacturer. Doing so will help ensure fresher-tasting ice and prevent potential clogging of water lines. Regular inspections of the water inlet valve and line can help identify leakage issues that can lead to water damage and affect ice quality. Homeowners can take preventive measures to reduce breakdowns and ensure clear ice cubes.
When It’s Time for a Repair or Replacement
Ice makers are incredible appliances designed to provide an endless supply of ice, but even with diligent maintenance, they are not immune to wear and decay. Suppose you notice a decline in ice production, water leakage, or strange sounds during operation. These signs indicate that the ice maker might require professional servicing or a complete replacement. Discolored ice cubes could suggest the presence of mineral deposits in the water line or rust inside the system, and these issues require immediate attention to prevent further damage. By recognizing these signs early, appliance owners can take swift action, potentially warding off costlier repairs or full-system failures. It is essential to stay alert and care for your ice maker to ensure it operates efficiently and effectively.
Ease of Troubleshooting Common Ice Maker Issues
A proactive approach often resolves many ice maker issues without expert intervention. Some common problems, such as stalling of ice production, can be tackled with straightforward measures like checking for a blockage in the fill tube or ensuring strong water flow for the ice maker’s operation. Detectable frost or icy buildup usually signals a damaged seal or gasket, which can permit outside air to infiltrate and cause unwanted frost—a simple gasket replacement could be the quick fix. Unpleasant tasting or smelly ice often necessitates cleaning the ice bin or changing the water filter to rid the system of the cause of odor or contamination. Such basic troubleshooting techniques can usually save homeowners both time and expenses.
Selecting a Replacement Ice Maker
If your refrigerator’s ice maker reaches the end of its functional lifespan or suffers irreparable damage, selecting the correct replacement is critical. The market offers a diverse range of ice maker models that can be fitted to various refrigerators. Opting for a compatible unit ensures smooth operation and decreases the likelihood of future malfunctions. In such scenarios, the appliance’s model number is your trusty reference, guiding you to the precise part that will complement your refrigerator seamlessly.
Environmental Impact of Ice Makers
As people become increasingly aware of environmental concerns, they are paying more attention to household appliances’ impact on the planet. Refrigerators, in particular, are being scrutinized for their high energy consumption and ecological footprint. This has led to a growing concern about ice makers, which are essential to refrigerators and contribute significantly to their energy usage. As a result, consumers are seeking more eco-friendly options for their refrigeration needs. It’s worth noting that modern ice makers are increasingly designed to be more energy-efficient and are often incorporated into energy-saving refrigeration solutions. By referring to resources such as the Energy Star Criteria for Refrigerators, environmentally conscious individuals can make informed and sustainable choices when selecting eco-friendly appliances.
BUSINESS
Data Detectives: How Your Participation in Clinical Trials Advances Medical Science
Key Takeaways:
- Understanding the integral role of clinical trials in medical progress.
- Recognizing the benefits and risks of clinical trials to participants.
- The ethical considerations and the importance of informed consent.
- How data from trials can shape the future of healthcare.
Table of Contents:
- The Foundations of Clinical Trials
- Volunteer Engagement: The Heart of Discovery
- Demystifying the Clinical Trial Process
- The Significance of Informed Consent
- Efficiency and Ethics: The Dual Priorities
- Behind the Scenes: Data Analysis in Trials
- Impact on Future Medicine
- How to Become a Clinical Trial Volunteer
The Foundations of Clinical Research
Clinical research is the critical cornerstone of medical advancements, reflecting the symbiosis between scientific rigor and human volunteerism. These protocols are essential for ascertaining emerging medical interventions’ safety and efficacy and ensuring continued treatment options development. The grounding principle of any clinical trial is the structured framework that guides its processes. This framework is methodically designed and subject to intense scrutiny by regulatory bodies, ensuring that new therapies are effective and safe for the populace. The structured nature of clinical research allows professionals to take logical and measured steps toward breakthroughs in medical science.
Volunteer Engagement: The Heart of Discovery
At the fulcrum of all clinical research efforts are the trial participants themselves. These individuals, often called volunteers, play an invaluable role in discovering new treatments. By agreeing to partake in trials, they provide a service that transcends personal benefit. They contribute to a broader societal good, encompassing enhanced knowledge about disease processes, potential treatments, and therapeutic interventions. Acknowledging the benefits and risks of clinical trials is pivotal to participant involvement. Volunteers are thoroughly briefed on possible side effects, anticipated outcomes, and the crucial nature of their contribution, thus enabling them to make informed decisions and be active, informed contributors to the trial process.
Demystifying the Clinical Trial Process
Many people may find the clinical trial process opaque and complex, fraught with scientific jargon and intricate procedures. Breaking down these barriers to understanding is crucial for enhancing public engagement and transparency. It is typically segmented into a series of phases, each meticulously design to serve a particular purpose. Phase I trials act as a safety check for a new intervention on a limited number of participants, while Phase II studies involve a larger group to evaluate its effectiveness. After completing these stages, Phase III trials are conducted on a larger scale, comparing the intervention with existing treatments to establish superiority or equivalence.
The Significance of Informed Consent
Informed consent is a crucial pillar of clinical research, acting as a gateway for participant autonomy and safety. This process involves educating potential participants about the clinical trial understandably and comprehensively. The informed consent form details every aspect of the trial, such as the nature and purpose of the research, anticipated risks and benefits, alternative procedures or treatments, and the participant’s rights, including the right to withdraw from the trial at any time. This transparency protects the volunteer and fosters an environment of trust and ethical practice within the trial. Allowing participants to enter the study with a complete understanding of their involvement is a moral obligation and cornerstone of compassionate research practices.
Efficiency and Ethics: The Dual Priorities
Clinical research operates on two inextricably linked priorities: efficiency in data collection and unwavering commitment to ethics. Researchers seek to obtain robust and high-quality data that can withstand scrutiny and form the basis for medical guidelines and treatment protocols. Simultaneously, the ethical considerations in clinical trials encompass participant privacy, informed consent, risk minimization, and the equitable selection of research subjects. These measures ensure that pursuing scientific knowledge does not compromise human dignity and respect for individual rights.
Behind the Scenes: Data Analysis in Trials
The success of clinical research is inherently tied to the meticulous analysis of the data it generates. Teams of statisticians and data scientists work in the background, sifting through vast amounts of information to identify trends, outcomes, and potential issues. The data analysis phase is meticulous and delicate, as it holds the key to validating the effectiveness of new medical interventions. During this phase, the results are interpreted to derive conclusions that could impact the availability of new treatments to patients worldwide.
Impact on Future Medicine
Clinical research is significant because it opens the possibility of new treatments and lays the groundwork for future innovations. Successful clinical trials have far-reaching implications; they inform clinical guidelines, contribute to scientific literature, and can significantly alter the course of patient care. In this sense, the data obtained from clinical trials is a valuable asset that can influence healthcare policy, funding allocations, and the standard of care delivered to patients globally for generations to come.
How to Become a Clinical Trial Volunteer
For those considering altruistic involvement in clinical trials, the path begins with understanding the eligibility criteria for participation and the depth of the commitment needed. Prospective volunteers should gather information on available trials that match their interests or conditions. The next step usually involves a pre-screening or an initial discussion with the trial coordinators, who provide detailed information on the trial’s scope and expectations. Making an informed decision to volunteer is not just a personal choice but a potential contribution to the collective medical advances.
For more information on the ethical and procedural nuances of clinical trials, interested individuals can consult global health authorities that offer resources and fact sheets for public education.
It’s critical to keep up with the most recent advancements in clinical research. News outlets often provide insightful coverage of current clinical trials and the strides in medical science, which can serve as a rich resource for learning about ongoing advancements.
BUSINESS
Winning in the Digital Aisle: Cutting-Edge Strategies for Grocery Success

Traditional grocery business models are being disrupted due to an extensive digital transformation, demanding a strategic re-think of retail practices. Companies need to stay relevant by adopting innovative strategies and embracing technological advancements. Within this evolutionary phase, loyalty programs have transcended their conventional role as dynamic tools for fostering customer fidelity and driving sophisticated marketing tactics. This article delves into practical and innovative methodologies that grocery businesses can capitalize on to flourish in today’s volatile market.
Table of Contents:
- Personalization in Grocery Shopping
- Enhanced Online Presence and E-commerce
- Supply Chain Optimization for Grocers
- Emerging Payment Systems in Grocery Retail
- Grocery Delivery Innovations
- Utilizing Big Data for Customer Insights
- Sustainability Practices in Modern Grocery Businesses
- Community Engagement and Support Strategies
- Conclusion
Personalization in Grocery Shopping
The importance of personalization in grocery shopping is rising as stores work to accommodate each customer’s unique requirements and preferences. With the integration of grocery loyalty programs, retailers can offer personalized discounts, recommendations, and incentives based on shopping habits and preferences. By analyzing data from loyalty programs, retailers can tailor promotions and offers to specific customers, enhancing their shopping experience and fostering loyalty. Customization boosts customer happiness and encourages recurring business by making them feel appreciated and understood. Personalization will become increasingly important in determining the future of grocery shopping as technology advances.
Enhanced Online Presence and E-commerce
Grocery companies must prioritize developing a solid online presence and making e-commerce infrastructure investments as more and more customers shop online for convenience and accessibility. This includes creating user-friendly mobile applications and websites that provide safe payment methods, easy navigation, and seamless browsing. Additionally, implementing click-and-collect or home delivery services enables customers to shop for groceries conveniently from their preferred devices. Grocery companies may reach a larger audience, adjust to changing consumer preferences, and profit from the expanding demand for online grocery shopping by embracing e-commerce.
Supply Chain Optimization for Grocers
Competent supply chain management is proving to be a cornerstone for ensuring the availability and freshness of products – attributes that drive a grocery store’s reputation and profitability. Advancements in real-time tracking, predictive analytics, and automated procurement systems have enabled grocers to control their inventories meticulously. As demand forecasting becomes more precise, grocery businesses can reduce overheads and avoid oversupply, thus championing sustainability and operational efficiency. Optimized supply chains are influential in maintaining product integrity and providing complete transparency from farm to fork, which is vital in securing consumer trust.
Emerging Payment Systems in Grocery Retail
Integrating innovative payment solutions within the grocery retail space underscores a commitment to convenience and customer satisfaction. The emergence of diverse payment solutions, such as mobile wallets and contactless card technologies, has set a new standard for transaction ease and speed. The rapid embrace of such payment mechanisms is a testament to the sector’s agility and focus on consumer-centric innovation. By simplifying payment processes, grocers enhance the shopping experience and drive efficiency in operational workflows – a dual advantage that can significantly improve the bottom line.
Grocery Delivery Innovations
The delivery service domain within grocery retail has witnessed transformative innovations driven by consumer demands for immediate and flexible service. Modern grocery delivery ventures encompass traditional home delivery and expedited services and subscription models that ensure a regular supply of household staples. Innovative logistics solutions are being explored, from crowd-sourced delivery networks to autonomous delivery bots and drones that promise to redefine convenience. These advancements optimize resource allocation and revolutionize the consumer’s perception of grocery fulfillment.
Utilizing Big Data for Customer Insights
A significant data era has sprouted unprecedented opportunities for grocery businesses to dial into deep customer insights. A strategic analysis of datasets encompassing sales figures, customer demographics, and purchasing behaviors leads to actionable intelligence that can guide everything from stock management to promotional ordeals. Grocery businesses that harness the power of big data analytics set themselves up for a future where retail strategies are data-driven and customer-centric, thus vastly outperforming competitors still reliant on traditional intuition-based practices. This data-oriented approach provides a bird’s eye view of the grocery market, allowing retailers to anticipate future trends and react swiftly.
Sustainability Practices in Modern Grocery Businesses
Sustainability has surfaced as a principal factor influencing consumer choices, and grocery stores increasingly embrace sustainable business practices. Initiatives around reducing carbon footprints, minimizing waste, and fostering local ecosystems exemplify a commitment to environmental stewardship. Retailers are positioned as champions of green initiatives by providing reusable packaging, energy-efficient store designs, and an emphasis on lowering the carbon emissions connected with logistics. Such practices resonate with consumer values and secure long-term resilience by aligning with global sustainability objectives.
Community Engagement and Support Strategies
Strengthening community ties through active engagement and support is an essential strategic pillar for grocery stores aspiring to become local staples. Through community-centric programs, neighborhood collaborations, and partnerships, grocery businesses underscore their role as critical contributors to local welfare. Supporting farmers’ markets, localizing supply chains, and participating in community events authentically demonstrates the grocery sector’s commitment to the societal fabric. These actions engender goodwill and a shared sense of purpose, fostering robust bonds with the communities they serve.
Conclusion
As the article unearths the pivotal role of digital transformation in shaping the grocery retail sector’s trajectory, it is clear that technology and innovation walk hand-in-hand with enhanced customer satisfaction and sustainable business practices. Seamless integration of online platforms, personalized experiences, supply chain intelligence, novel payment options, big data analytics, delivery logistical advancements, environmental stewardship, and community involvement encapsulate the manifold strategies underpinning the thriving grocery industry. These initiatives commend grocery businesses for their adaptability and point towards a future where technology and personal touch blend to transform the way we perceive grocery shopping.
-
 LOVE MESSAGES5 months ago
LOVE MESSAGES5 months agoSweet Love Messages for Her to Make Her Smile
-

 LOVE MESSAGES5 months ago
LOVE MESSAGES5 months ago100 Romantic Good Evening Messages For Her & Him
-

 LOVE MESSAGES5 months ago
LOVE MESSAGES5 months agoRomantic Love Messages For My Husband With Images
-
 LOVE MESSAGES5 months ago
LOVE MESSAGES5 months ago50 Just Checking on You Text Messages for Him & Her
-

 LOVE MESSAGES5 months ago
LOVE MESSAGES5 months agoSweet Love Messages For My Wife With Images
-

 LOVE MESSAGES5 months ago
LOVE MESSAGES5 months agoLong Good Morning Messages to Make Her Fall in Love
-

 LOVE MESSAGES5 months ago
LOVE MESSAGES5 months ago50 Cute Good Night Sweet Dreams Messages For Lovers
-

 LOVE QUOTES3 months ago
LOVE QUOTES3 months agoplease forgive me quotes her him images







